Hey there, fellow threat hunters! 👋 Today we're looking at MITRE D3FEND - ATT&CK's defensive cousin (or maybe brother). Let's see what it's about and how it can help us protect our systems, even with some of its current limitations.
| MITRE D3FEND main page |
While ATT&CK tells us how attackers operate, D3FEND (Digital Artifact Knowledge Graph) shows us how to defend against them. Born from a practical need to specify cybersecurity countermeasures more precisely, it's not just another framework - it's a knowledge graph that actually explains how defensive techniques work.
Fun fact: They analyzed over 500 cybersecurity patents from 2001 to 2018 to build this thing. Talk about doing your homework!
Breaking Down D3FEND
Unlike ATT&CK's TTPs, D3FEND uses a different structure:
Defensive Tactics
These represent broad categories of defensive approaches:
- Harden: Making systems harder to compromise
- Detect: Identifying malicious activities
- Isolate: Separating components to limit attack spread
- Evict: Removing adversary presence
- Deceive: Using deception to confuse attackers
Defensive Techniques
Each tactic contains specific defensive techniques. For example, under "Detect":
- File Analysis
- Network Traffic Analysis
- Process Analysis
- User Behavior Analysis
The D3FEND Reality Check
Let's be honest about where D3FEND stands:
Strengths:
- Clear mapping to ATT&CK techniques
- Structured approach to defense
- Good high-level categorization
- Semantically rigorous definitions
- Grounded in research literature
- Links defensive concepts to real-world implementations
Current Limitations:
- Some techniques lack detailed implementation guidance
- Not as extensively documented as ATT&CK
- Fewer real-world examples
- Some defensive categories could use more depth
- Still evolving (but hey, that's what the community feedback is for!)
Making D3FEND Work for You
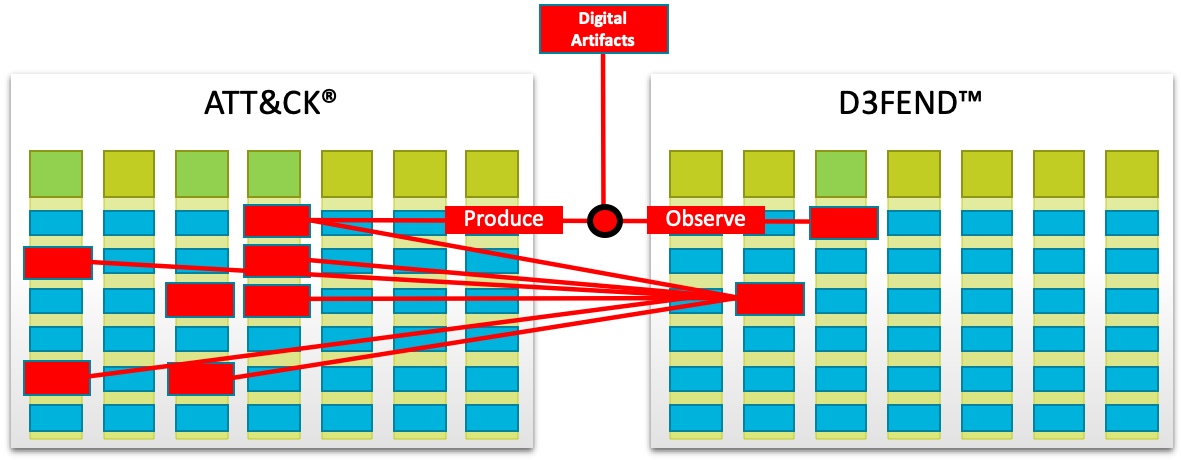 |
| Simplified Offensive and Defensive Technique Relationships (About the D3FEND Knowledge Graph Project) |
Despite its current limitations, D3FEND becomes quite useful when used alongside ATT&CK:
- Start with ATT&CK
- Identify your relevant threats
- Understand the attack methods
- Use D3FEND as a Guide
- Map defensive categories
- Use available technical details
- Fill gaps with industry knowledge
- Document Your Approach
- Note where D3FEND helps
- Supplement with your own research
- Share knowledge with the community (they literally ask for it!)
Practical Application
| File Content Analysis (D3-FCOA) |
Let's look at a real example:
ATT&CK Technique: T1566.001 (Spearphishing Attachment) D3FEND Countermeasures:
- Message Analysis
- File Analysis
- Network Traffic Analysis
While D3FEND might not detail every implementation aspect, it gives us a solid framework to build upon. What makes it special is that it doesn't just tell you what to do - it explains how these defenses actually work under the hood.
Remember: D3FEND is a relatively new framework that's actively growing through community feedback and research. Like any security tool, it's not perfect, but it's still valuable when used appropriately. Use it as a starting point, not a complete solution.
Stay safe, and happy defending.

